Top Stories
And when such a call is combined with any act that seizes or destroys a strategic target, takes hostages, impedes civilian mobility, cripples supply lines, delays emergency response, or poses a threat of mass casualties, it should be understood and treated as such. Tom Cotton’s open encouragement of terrorists’ would-be victims in their own defense reflects the moral clarity necessary to discern terrorism from political protest…
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
The Dean’s List with Host Dean Bowen – The Supreme Court rules that Idaho’s law banning gender surgeries on minors can take effect during ongoing litigation. This decision marks a significant victory for those advocating for legislative protection of children from life-altering procedures. The law also restricts medical professionals from prescribing puberty blockers and hormones, citing health concerns…
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
Dr. Li-Meng Yan w/ The Voice of Dr. Yan – Xi: Do not be so afraid of war. The old guy Bi (= Joe Biden) made it very clear that there will be no hot war between the nuclear States. If there is a hot war between the nuclear States, human beings and the earth will be destroyed. This is the rule set by the United States after World War II when they built the nuclear bomb…
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
America Out Loud PULSE with Dr. Vaughn & Dr. Tankersley –Sen Ron Johnson’s interview this past week with New American was more insight from the most honest senator regarding the huge catastrophe of COVID. His awareness of the deceptions of Fauci et al. was earlier than any politician we are aware of. He details Fauci’s deceptions from the start – IT IS UNDENIABLE…
Featured Offer Link to our SHOP
Upcoming Schedule
Here, we take on the challenges of our generation so that we can preserve future generations.
Newsfeed
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
Truth Be Told with Booker Scott – In 2021, the top 50% of filers earned 90% of all income, so half of Americans are earning 9 out of every 10 dollars. It would be easy to think that a fair share would be 90%; that’s fair, isn’t it? I’m not sure how much fairer Biden wants it and where he thinks he’s going to get it because that same 50% of filers pay 98% of all taxes the government receives…
Too often, peer review of scientific reports amounts to little more than “pal review,” a rubber stamp from supporters of the hypothesis being investigated. What is needed is to allow reports to be reviewed by many people on all sides of issues, both inside the scientific community and in the public at large. One prominent group is actually doing this — the London, UK-based Global Warming Policy Foundation…
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Podcast Index | Email | RSS
Nurses Out Loud with Kimberly Overton, BSN, RN – We explore the vibrant resurgence of patriotism among the younger generation, highlighting the profound impact of national pride. We delve into the story of Tyler Shepard, a Pararescueman turned entrepreneur, whose life and ventures embody the enduring spirit of American values and the transformative power of dedicated citizenship in the 21st century…
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
Looking 4 Healing Radio with Dr. Henry Ealy – Dr. H recounts this experience and other brushes with death in his life. From a young age, he learned that the inevitability of death is not something to be feared but appreciated for its ability to help us live a life of joy and wonder. Our time on this earth is limited, and we get to choose the legacy we will leave behind, always knowing there is something better waiting for us on the other side…
Having our military dollars going to an endless war in Ukraine and toward shooting down an endless supply of rockets and missiles over Israel helps China reach parity with our military. Banning all cars except those made with rare earth materials, it’s illegal to mine in the United States helps China’s economy, as does shuttering all forms of reliable and affordable energy. Our country is committing economic and political suicide…
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
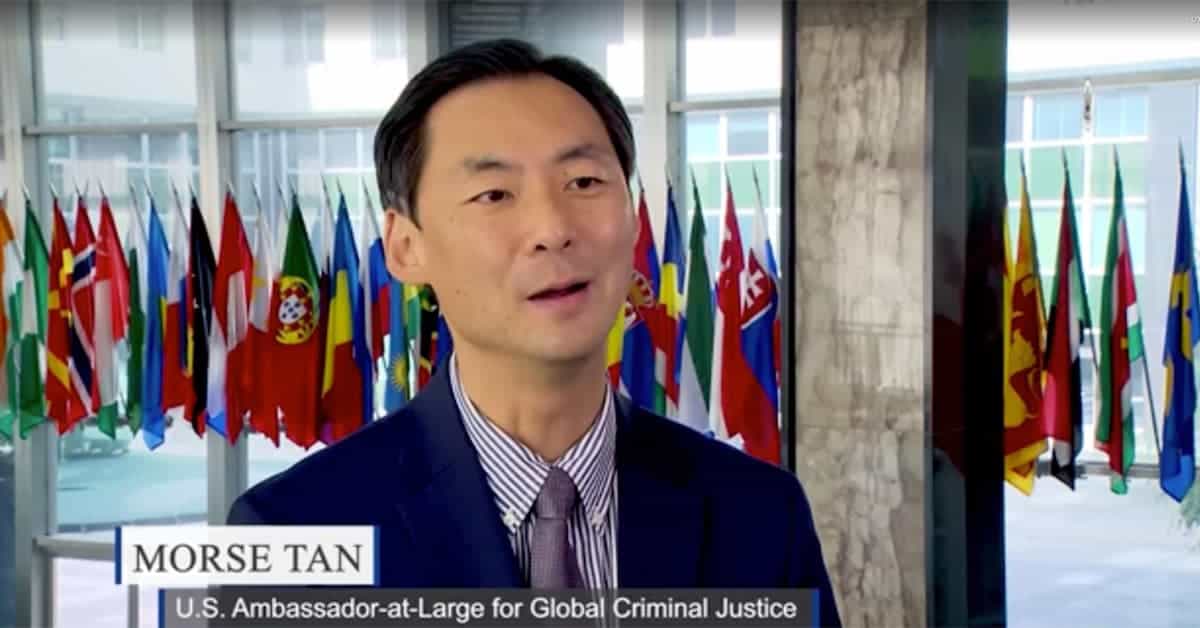
The National Security Hour with Col. John Mills Ret. – Ambassador Tan, serving during the Trump Administration, achieves significant milestones at the State Department. He holds the Chinese Communist Party accountable for genocide against the Uyghurs and highlights abuses against other groups. Despite facing hostility, he champions diplomacy over military action, contrasting with the approaches of subsequent Democrat administrations under Biden…
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
The Tom Renz Show – Scott McKay, the Patriot Streetfighter, is relentlessly fighting to keep this country safe. I’ve had the privilege of working with Scott for several years now, and he doesn’t pull punches; he sticks to his principles. On May 10 and 11th, he is bringing his Patriot Preparedness Symposium to Ohio, and I’m looking forward to speaking and being with so many awesome patriots. Let’s keep the fight for freedom going with Scott today on the show.
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
The Constitution Study with Host Paul Engel – The Foreign Intelligence Surveillance Act (FISA) is misused to spy on Americans, including political figures and protestors. As Congress debates renewing Section 702, concerns grow about continuing abuses of power and the erosion of civil liberties. Remember Benjamin Franklin’s warning about sacrificing liberty for security as we face another potential renewal of these invasive powers.
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
The Dean’s List with Host Dean Bowen – Idaho legislators champion common sense, passing a bill to ban compelled speech in public schools and government entities. Effective July 1, this legislation ensures that no one in Idaho is forced to express beliefs they disagree with, protecting free speech rights. It’s a step towards safeguarding individual freedoms against coercive practices in educational settings.
What is happening is not by accident; what is taking place is a coordinated effort to import as many ‘bad guys’ into America as possible, with the ultimate goal of “fundamentally transforming” the United States of America. But transforming America into what? It’s pretty obvious to any objective observer what is underway, which is nothing less than an attempt to overthrow our free market Capitalist system and replace it with…
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
After Dark with Hosts Rob & Andrew – Even many legal experts on the left and right have come out to say the charges facing Trump are ridiculous, and no prosecutor would want to prosecute. But somehow, the current district attorney, Alvin Bragg, a Progressive Democrat, decided to resurrect the charges and elevate them to a felony. Oh, and by the way, he, too, had passed on charging Trump because he, too, saw “no there…there.”
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
The Constitution Study with Host Paul Engel – Depending on what news outlets you pay attention to, you’ll hear claims of government corruption. Of course, these outlets and the people who trust their reporting will disagree about who in government is corrupt and what policies are corrupt, but we all pretty much agree that there is corruption. Unless we recognize our own biases and those of those we get our news from, we will forever be…
Featured Books Link to America Out Loud Bookstore
Cultural Wars
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Podcast Index | Email | RSS
Nurses Out Loud with Kimberly Overton, BSN, RN – We explore the vibrant resurgence of patriotism among the younger generation, highlighting the profound impact of national pride. We delve into the story of Tyler Shepard, a Pararescueman turned entrepreneur, whose life and ventures embody the enduring spirit of American values and the transformative power of dedicated citizenship in the 21st century…
Healthcare
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
Looking 4 Healing Radio with Nichola Burnett – Being in a relationship with our bodies is really no different from being in a relationship with a friend to whom you would provide respect, care, and honor. One of the ways we show respect, care, and honor to what should be our best friend, the body, is by tuning in and listening and paying attention to these miraculous flesh suits that the Creator has blessed us with…
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Podcast Index | Email | RSS
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
2024 Elections
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
Podcast: Play in new window | Download | Embed
Subscribe: Apple Podcasts | Email | RSS
What is happening is not by accident; what is taking place is a coordinated effort to import as many ‘bad guys’ into America as possible, with the ultimate goal of “fundamentally transforming” the United States of America. But transforming America into what? It’s pretty obvious to any objective observer what is underway, which is nothing less than an attempt to overthrow our free market Capitalist system and replace it with…